CyberArk is a security program that manages passwords to safeguard privileged accounts. It safeguards preferred accounts for corporations by automatically keeping passwords. With the aid of the CyberArk tool, we can save and keep data by converting the credentials of accounts that can successfully fight against malware and hacking threats. It is a highly defensive technology. It is used in a variety of areas, including healthcare, finance, retail, and financial services. A privileged account is one that has access to information such as social security numbers, PHI, credit card details, and so on. Privileged accounts in certain companies include domain admin accounts, local admin accounts, privileged user accounts, service accounts, application accounts, emergency accounts, and so on.
Main Characteristics of CyberArk
- CyberArk PAS guarantees security and keeps track of privileged passwords, SSH keys, and other sensitive data.
- It adds accounts to the pending list in order to validate privileges or to automatically onboard and rotate them.
Isolate
CyberArk PAS encrypts jump servers and monitors credentials in a separate environment.
- It connects to a safe jump server through a number of native procedures.
- It defends against harmful software assaults and manages privileged access.
Audit
- It records privileged sessions and saves them in a central database.
- Automatically validates the video recording records.
- It starts picturing the most dangerous sessions first, at the point where the most suspicious actions are taking place.
Monitor
- It depicts the favorite activity by jumping to certain activities, keystrokes, and so forth.
- Based on risk actions, it automatically notifies SOC and IT administrators.
- It lowers the number of accounts that can get around privileged restrictions.
Remediate
- Depending on the risk score and the action, it immediately suspends or shuts privileged sessions.
- In the case of a hack or theft, it automatically rotates credentials depending on risk.
Privileged Access Security Architecture from CyberArk
Privileged Access Security Solution offers a secure location for the business where all administrative passwords. It may be safely transmitted, preserved, and shared by authorized users such as IT personnel, on-call administrators, and local administrators at remote locations.
CyberArk Privileged Access Security is a multi-layered system for storing and distributing passwords across the business. VPN, authentication, encryption, firewall, access control, and so on are examples of these levels. CyberArk Privileged access security architecture consists of the following components:
Engine for storing data
A storage engine is refer as a vault or a server. It contains the data. It guaranteed data security as well as validated and restricted access.
Interface
The interface is in charge of interacting with the storage engine and granting users and programs access. The vault protocol, a secure CyberArk protocol, is used to communicate between the storage engine and the interface.
Let’s see how these components are linked in the CyberArk architecture:
-
Digital Vault by CyberArk
This is a secure network site where the most sensitive data store. To totally isolate the data, the vault is designed to be placed on a separate computer. When installed, it comes packed with cutting-edge security technology and is all set up and ready to use. This means that the system does not require any sophisticated configuration or security skills to run at full capacity. It is critical to have continual access to your password. Access to your passwords may be temporarily restricted if a server breaks. The vault can build as a cluster of high-availability servers that enable constant access to vault accounts.
-
Web Access Interface for Password Vault
It is a web interface that provides a centralized portal for end-users and administrators to request, access, and manage preferred passwords throughout the organization. Each user’s dynamically produced list of frequently used passwords makes it simple to retrieve and use them fast. It also gives users access to Privileged accounts, allowing for seamless communication and optimal workflows. The PVWA wizard is straightforward and easy to use, allowing users to create new preferred passwords.
A strong search tool, on the other hand, allows you to look for passwords and sensitive information with no effort. The PVWA dashboard displays an activity overview of your Privileged Access Security Solution, as well as data on all actions that occurred. These dashboards display a graphical representation of the managed passwords as well as links to specific information about users and passwords that require extra attention.
-
Client of PrivateArk
The PrivateArk client is a window program that serves as an administrative interface for the PAS solution. It is install unlimited number of distant computers and accesses the vault via any combination of local area network, wide area network, and the Internet. To get access to the vault, the vault administrator must specify the users in the vault as well as the IP address of the machine on which the PrivateArk client is installed.
Before accessing the vault, the user required authorization. With a customized combination of passwords, physical keys, and certificates, the PAS system delivers extremely secure user authentication. Following authentication, a user may use the PrivateArk client to create a vault hierarchy, as well as safes and users. Users also monitor and track actions such as who accesses the information, where it is accessed, and when it is accessed. To provide optimum data privacy at all times, each request, command, user configuration, and file transfer is encrypted before being communicated between the vault and the PrivateArk customer.
Manager of Central Policy
The Privileged Access Security Solution, may change passwords on distant devices and store new passwords without the interaction of a person. The CyberArk Central Policy Manager is not able. It also enables businesses to check credentials on remote sites and restore them if needed. CPMs can place on various networks to handle credentials that are all stored in a single vault. According to the Privileged Access Security solution’s distributed design. The vault also supports shared config files for extra GPCs in high availability systems and password management per safe in load-balancing deployments. The PAS solution’s versatility allows it to accommodate complicated dispersed situations.
Manager of privileged sessions
Organizations may use Privileged Session Manager to regulate, monitor, and secure privileged access to network devices. PSM employs vaulting technology to manage access to privileged accounts at a centralized location, allowing a control point to initiate privileged sessions. PSM include policies that govern the users to permit access to privileged accounts. When they permitted to do so, and for what purpose. It also restricts which connection protocols a user may access by allowing the organization to filter banned protocols. It captures privileged session actions in a compact manner, giving complete session audits and DVR-like replay. This recording is safe and save on the vault server, where authorized auditors can view them.
SSH Privileged Session Manager
Using PSM for SSH, an organization may monitor, regulate, and secure privileged access to network devices. It can manage access to privileged accounts at a centralized location with the use of vault technology, permitting a control point to commence privileged sessions. PSM for SSH determines which users have the authority to utilize privileged accounts and initiate privileged sessions, as well as when and why they do so. PSM for SSH may record all activity that occurs in the selected session in a concise style. Text recording encrypt. It’s keep on a vault server, where authorized auditors can view them. PSM for SSH supports single sign-on and allows users to access target devices without exposing privileged connection credentials.
Manager of On-Demand Privileges
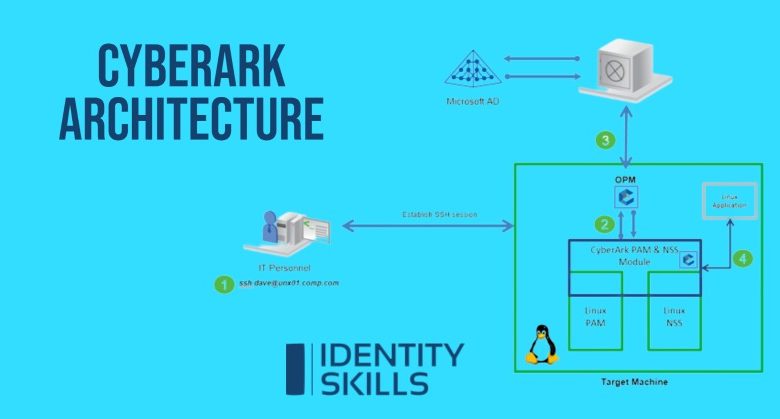
With the use of Vaulting technology, CyberArk’s On-demand Privileges Manager enables businesses to monitor, restrict, and protect privileged access to UNIX commands, allowing users to complete work with their personal accounts while adhering to the least privileged principle. It provides a comprehensive solution that enhances IT and enables total visibility and management of super-users and privileged accounts across the company. With the support of OPM, the Privileged Access Security solution enables centralized control and auditing in all elements of privileged account management.
Analytics for Privileged Threats
A privileged account is a part of an attack. CyberArk Privileged Threat Analysis monitors the use of the privileged accounts managed. The CyberArk Privileged Access Security platform account is not managed. CyberArk searches for indications of misuse or abuse of the CyberArk platform. PTA carries out complex assaults like Golden Ticket and looks for attackers who penetrate privileged accounts. PTA is a component of the CyberArk PAS solution that adds an additional layer of protection by detecting malicious activity generated by privileged accounts and proactively containing active assaults. When a privileged account is authenticate using passwords or SSH keys, PTA detects malicious activities.
Uploader for Passwords
The password Upload tool uploads multiple password objects to the Privileged Access Security Solution, which speeds up and automates the Vault installation process. It operates by uploading passwords and their bulk characteristics to the vault from a pre-prepared file and, if necessary, generating a suitable environment.
APIs for administration
The CyberArk Vault Command Line Interface allows users to employ automated scripts in a very intuitive command-line environment to access the Privileged Access Security system from anywhere.
Interfaces for SDKs
The Application Password SDK eliminates the need to save the application password with the application, configuration files, or scripts. This sensitive credential is central, managed, and tracked inside the PAS solution. This novel solution will help enterprises to meet internal and regulatory needs to reset passwords on a regular basis. As monitor desired access to all systems, apps, and databases.
The Application Password SDK includes APIs for.Net, Java, CLI, C/C++, and COM. The Application Password Provider is a “local server” that securely stores passwords received from the vault. Application Password provider gives rapid access to passwords of network performance. Application Server Credential Provider secures and automates the management of application server credentials stored in XML data source files. It eliminates the need for any application code changes and allows for password substitution without having to restart the application server. Downtime is eliminated, and business continuity is ensured.
Here, we learn about CyberArk and its architecture from the above blog. I hope you find the material on this blog to be helpful. We’ve covered all there is to know about the CyberArk architecture. If you notice that any aspect of CyberArk architecture is missing, or if you believe something should be added, please follow our Online Cyberark Training.




